Web Security Attacks: Types, Scenarios, and Examples
Introduction
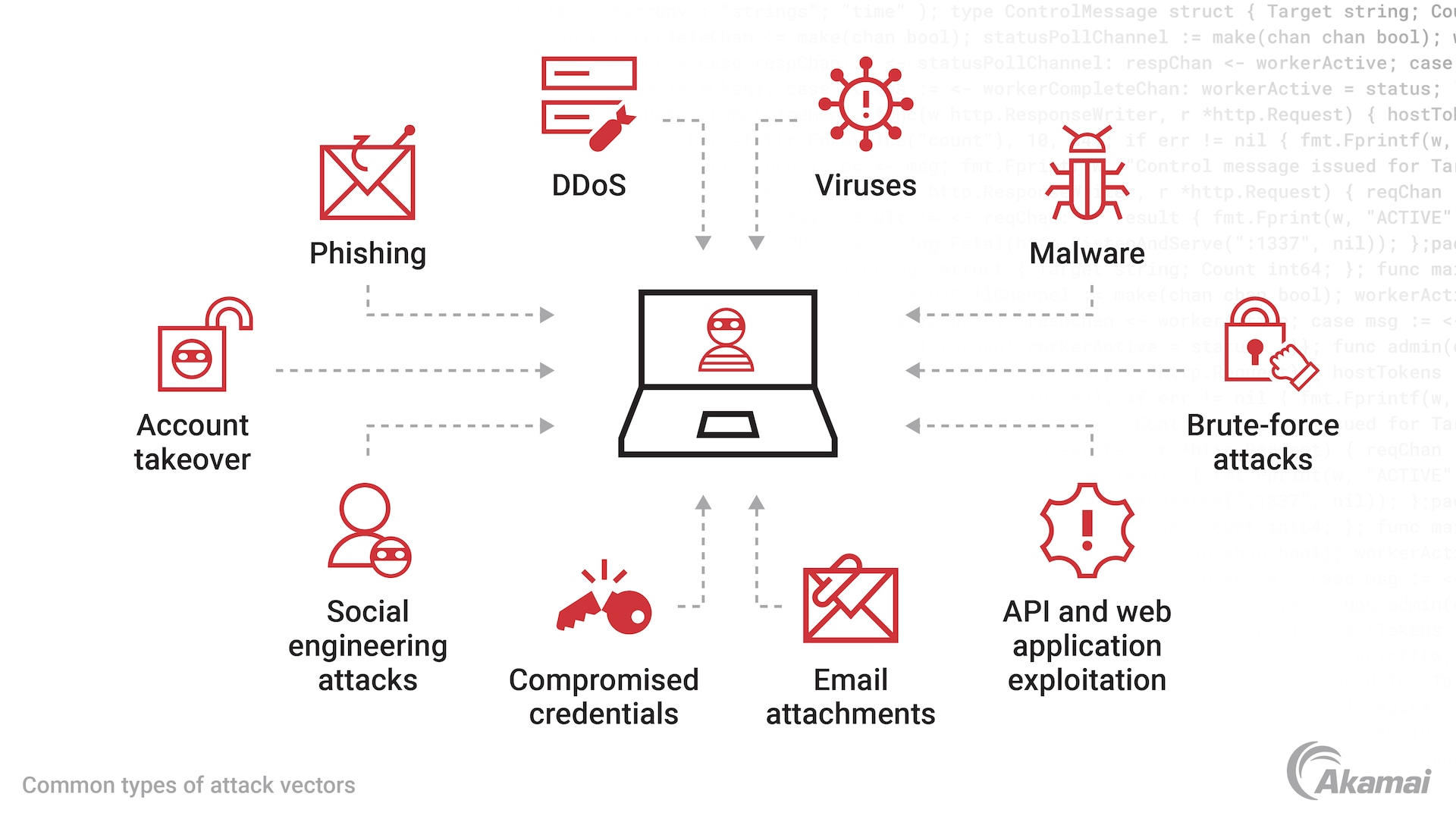
With the increasing reliance on web applications and online services, ensuring robust web security is paramount. Web security attacks pose significant threats to websites, applications, and user data. In this article, we will explore various types of web security attacks, along with scenario examples, to understand their impact and learn how to protect against them.
Table of Contents
- 1. Cross-Site Scripting (XSS) Attacks
- 2. SQL Injection Attacks
- 3. Cross-Site Request Forgery (CSRF) Attacks
- 4. Clickjacking Attacks
- 5. Distributed Denial of Service (DDoS) Attacks
- 6. Scenario: Cross-Site Scripting (XSS) Attack
- 7. Scenario: SQL Injection Attack
- 8. Mitigation and Prevention
1. Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting (XSS) attacks involve injecting malicious scripts into web pages viewed by users. Attackers exploit vulnerabilities in web applications that allow user-supplied data to be improperly handled and executed by browsers. This can lead to the execution of unauthorized scripts, data theft, or session hijacking.
2. SQL Injection Attacks
SQL Injection attacks occur when an attacker inserts malicious SQL statements into a web application's input fields. If the application fails to properly sanitize or validate the input, the attacker can manipulate database queries, potentially gaining unauthorized access to sensitive data, modifying or deleting data, or even executing arbitrary commands.
3. Cross-Site Request Forgery (CSRF) Attacks
Cross-Site Request Forgery (CSRF) attacks trick authenticated users into unknowingly performing malicious actions on a website. Attackers create specially crafted requests that exploit the trust between the user's browser and the target website. This can lead to unauthorized changes in user settings, actions performed on their behalf, or data leakage.
4. Clickjacking Attacks
Clickjacking attacks deceive users into clicking on hidden or disguised elements on a website, while the user believes they are interacting with something else. Attackers overlay transparent or opaque elements on top of legitimate website content, tricking users into unknowingly performing actions they did not intend, such as clicking on malicious links or granting permissions.
5. Distributed Denial of Service (DDoS) Attacks
Distributed Denial of Service (DDoS) attacks overwhelm web servers, networks, or applications by flooding them with a massive volume of traffic. Attackers typically employ botnets, which are networks of compromised devices, to generate the traffic. This can result in service disruptions, rendering the targeted website or application unavailable to legitimate users.
Scenario: Cross-Site Scripting (XSS) Attack
Scenario: Imagine a situation where a user visits an online forum and encounters a post containing a malicious script. The script, injected through a vulnerable input field, targets the user's session cookies. When the user views the post, the malicious script executes in their browser, stealing their session cookies and allowing the attacker to impersonate the user, potentially gaining unauthorized access to their account.
Scenario: SQL Injection Attack
Scenario: Consider a situation where a user submits a search query on a vulnerable e-commerce website. The website fails to properly validate and sanitize the input, allowing the attacker to inject malicious SQL code. As a result, the attacker gains unauthorized access to the database, retrieves sensitive customer information, and potentially modifies or deletes data.
Mitigation and Prevention
To protect against web security attacks, consider the following mitigation and prevention techniques for each attack type:
Cross-Site Scripting (XSS) Attacks
- Implement proper input validation and output encoding.
- Use security libraries and frameworks that automatically sanitize user input.
- Employ secure coding practices and stay updated on web application vulnerabilities.
SQL Injection Attacks
- Utilize parameterized queries or prepared statements with parameter binding.
- Validate and sanitize user-supplied input to prevent malicious SQL code injection.
- Regularly perform security assessments, code reviews, and apply security patches.
Cross-Site Request Forgery (CSRF) Attacks
- Implement anti-CSRF tokens or use same-origin policy mechanisms.
- Ensure user actions require explicit consent to prevent unauthorized requests.
- Educate users about the risks and best practices to avoid CSRF attacks.
Clickjacking Attacks
- Implement X-Frame-Options headers or Content Security Policy (CSP) directives.
- Employ frame-busting techniques to prevent framing of website content.
- Regularly test and validate the effectiveness of implemented defenses.
Distributed Denial of Service (DDoS) Attacks
- Deploy traffic filtering and rate-limiting mechanisms.
- Utilize load balancing and content delivery networks (CDNs) to distribute traffic.
- Consider using DDoS protection services or solutions to detect and mitigate attacks.
By implementing these mitigation and prevention techniques, web applications can be fortified and the risks posed by web security attacks can be significantly reduced.
Conclusion
Web security attacks pose significant risks to websites, applications, and user data. Understanding the different types of web security attacks and their techniques is crucial for developers, administrators, and users to protect against them. By implementing secure coding practices, input validation, output encoding, and employing appropriate security measures, we can fortify web applications and mitigate the risks posed by these attacks.
Note: This article provides an overview of various web security attacks and scenario examples. It is essential to stay updated on the latest security vulnerabilities, patches, and best practices to ensure the security of web applications and protect against emerging threats.